Securonix, a cybersecurity firm, has discovered a new malware campaign called ‘GO#WEBBFUSCATOR,’ which uses space photos from the James Webb telescope to transmit malware.
The malware is developed in Golang, a programming language that is gaining popularity among cybercriminals primarily due to its cross-platform capabilities and resistance to reverse engineering and analysis.

According to Securonix, antiviruses are still not detecting the malware-laden image.
The hacker targets victims using spam emails containing a malicious Office document designed to download malware onto the victim’s computer automatically. During the process, Securonix discovered that the programme had a photograph captured by the James Webb Space Telescope.
The image is a jpg file that appears to be an interesting picture of an area of space known as SMACS 0723, which the space telescope captured earlier this year. However, according to Securonix, the file contains secret computer code that can be seen by inspecting the image using a text editor.

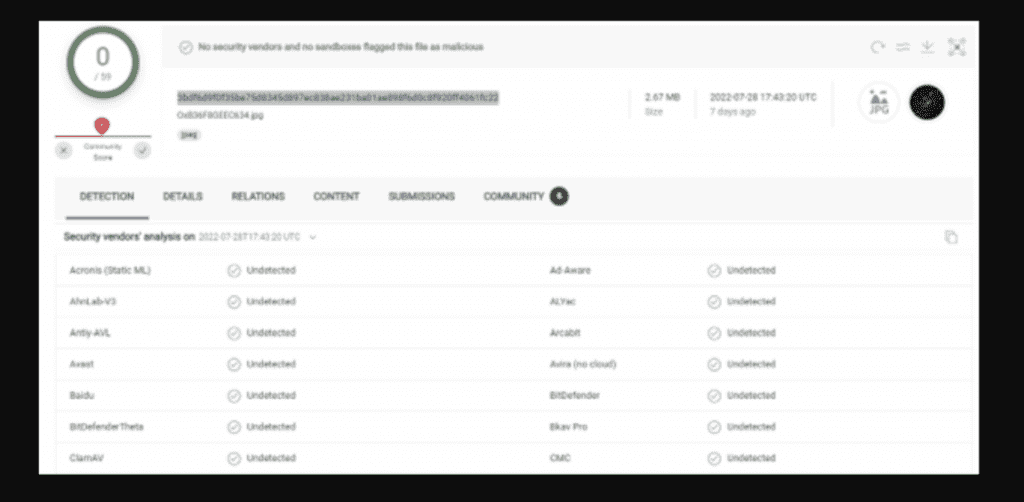
“The image contains malicious Base64 code disguised as an included certificate. At the time of publication, this particular file is undetected by all antivirus vendors,” Securonix wrote in a blog post.
The underlying computer code is the basis for the main malicious program. The malware explicitly decodes the computer code in the picture file and converts it into a Windows 64-bit programme called msdllupdate.exe, which may be executed on the Windows system.
Securonix examined the malware and discovered that it will attempt to persist on a Windows PC by inserting a binary programme “into the Windows registry Run key.” This will force the malware to run every time the computer boots up. The malware is also programmed to accept commands and communicate with the hacker’s command and control server. As a result, the hack can allow cybercriminals to eavesdrop on or remotely take over an infected system.
This is hardly the first instance of a hacker using images to transmit malware. Security experts have observed that cybercriminals use images to hide malware infections or communicate with malicious programmes throughout the years.
Securonix cautions that, in this case, the malicious files that start the attack can only do so if Office products’ “child processes” and macros are enabled. The hacker’s techniques won’t be able to run automatically otherwise.