The rise of keyless thefts in the UK has led to a cybersecurity researcher becoming a victim of this sophisticated crime.
Ian Tabor, the owner of a Toyota RAV4, noticed that his car was missing the front left-side bumper, and the headlight was partially dismantled twice in three months. After his car was stolen, Tabor discovered that he was a victim of a new and sophisticated technique called CAN injection attacks, which bypass the entire smart key system. CAN injection attacks involve the attacker injecting malicious messages into a car’s Controller Area Network (CAN) to take over the car’s internal systems.

Tabor, with the help of fellow automotive security expert Ken Tindell, reverse-engineered an “emergency start” device to uncover this new attack. In addition, Tabor and Tindell designed two defenses that could defeat CAN injection attacks, but Toyota has yet to respond to their notification.
In the investigation, Tabor analyzed the telematics system Toyota uses to track vehicle anomalies known as Diagnostic Trouble Codes. He found that his car had recorded many DTCs around the time of the theft, showing that communication had been lost between the RAV4’s CAN and the headlight’s Electronic Control Unit. In addition, the failure of many other ECUs suggested that the CAN bus had malfunctioned.
Tabor then turned to crime forums on the dark web and YouTube videos discussing how to steal cars, where he discovered ads for “emergency start” devices. He bought a device advertised for starting various vehicles from Lexus and Toyota, including the RAV4, for reversing engineering it and figuring out how it worked on the RAV4’s CAN. This research uncovered a new form of keyless vehicle theft that involved CAN injection attacks.
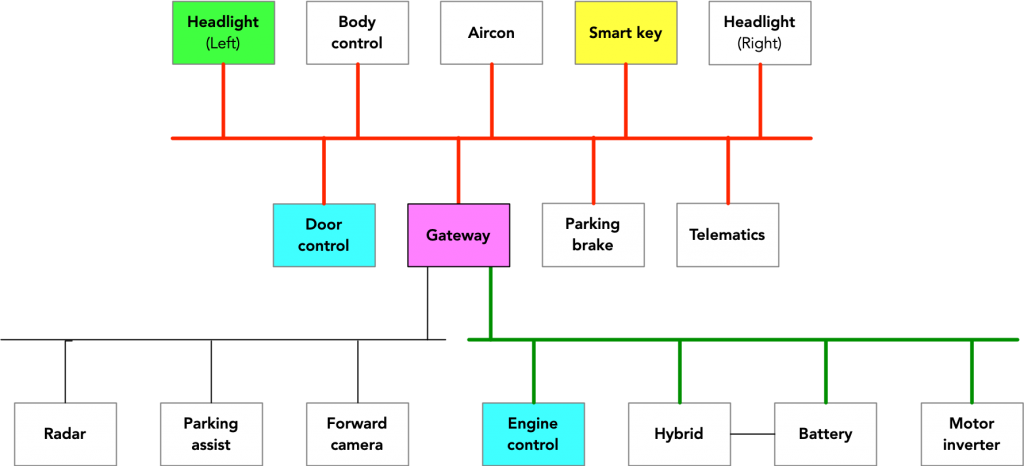
Tabor’s investigation found that CAN injection attacks involve the attacker injecting malicious messages into a car’s Controller Area Network (CAN) to take over the car’s internal systems. The CAN injector Tabor bought was disguised as a Bluetooth JBL speaker to give thieves cover in case police or others become suspicious.
A closer analysis revealed that CAN injector chips were grafted to the circuit board. Thieves use CAN injection attacks as a new way around the security of smart key systems following the defeat of relay attacks. Tindell has written about the need for car owners to keep their keys in a metal box to block the radio message from the car. Some car makers now supply keys that go to sleep if motionless for a few minutes and won’t receive the radio message from the vehicle.
In general, the rise of keyless thefts has led to the developing of new and sophisticated techniques, including CAN injection attacks. This recent attack bypasses the entire smart key system, leading researchers like Tabor and Tindell to design two defenses to defeat CAN injection attacks.
However, they are yet to receive a response from Toyota regarding their notification. With the rise of these attacks, car owners must take necessary precautions to protect their cars, such as keeping their keys in metal boxes and using keys that go to sleep if motionless for a few minutes.


