So a little context, there is an Intelligence firm called Cellebrite that is based in Israel. Their main products are phone cracking software that is designed to unlock phones and extract the data. Now, firms like these sell their software to pretty much anyone, any government as long as they can pay so they are pretty popular with most law enforcement agencies across the US.
Despite being software used to crack phones, the software itself doesn’t have that good of a security system in place. At least that’s what Signal’s CEO is telling us. Signal’s CEO Moxie Marlinspike claims to have broken Cellebrite’s security and has also explained how it can be manipulated.

Moxie published his findings in a blog spot on Signal’s website. He said that “We were surprised to find that very little care seems to have been given to Cellebrite’s own software security. Industry-standard exploit mitigation defenses are missing, and many opportunities for exploitation are present”.
This post came after Cellebrite announced that they added Signal support for their software. Moxie further added that “Until Cellebrite is able to accurately repair all vulnerabilities in its software with extremely high confidence, the only remedy a Cellebrite user has is to not scan devices”.
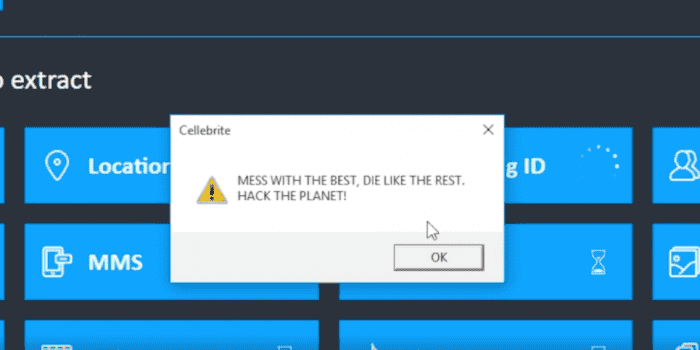
Moxie went as far as to include a fun video showing how to hack the software. You can view it in the tweet below.
Moxie appears to hell-bent on bringing Cellebrite to its knees. By hacking into their Physical Analyzer, Moxie claims that because of all of its security flaws, someone could basically re-write all the data the app extracts from phones. He explained that using a unique config file, that could be slipped on to the device being cracked, the hacker could alter everything the app may extract from it. Ultimately making the app useless.
The biggest claim from Moxie’s blog is that the app may just contain code that is the intellectual property of Apple. If this is true then Cellebrite is in for a world of hurt. The legal ramifications are huge. Selling code that might belong to one of its adversaries. According to the blog this “might present a legal risk for Cellebrite and its users”.
Cellebrite’s claims that it had cracked Signal’s encryption have just backfired on them hard.
“He who fights with monsters might take care lest he thereby becomes a monster. And if you gaze for long into an abyss, the abyss gazes also into you.”