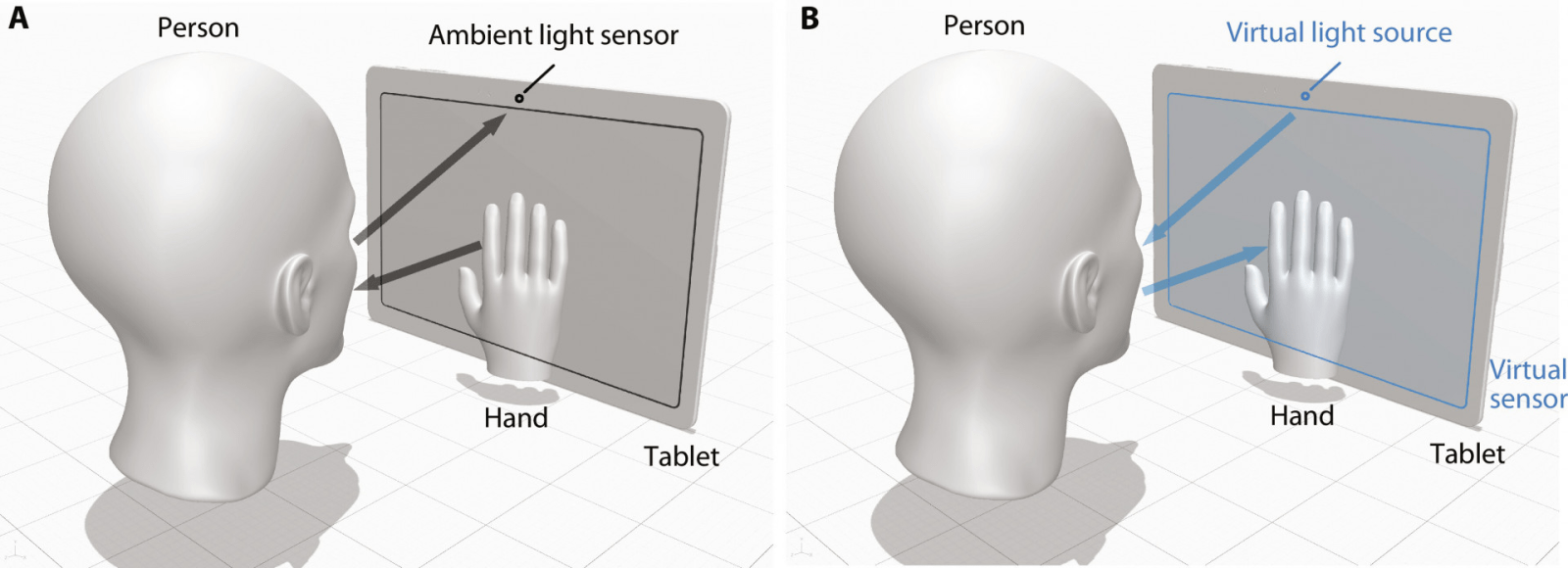
In a revelation with significant implications for digital privacy, MIT researchers have exposed a potential security vulnerability linked to smartphone ambient light sensors. Unlike traditional cameras, these sensors, responsible for adjusting screen brightness, can be exploited by hackers to capture images and monitor users’ hand gestures without their knowledge.
The researchers’ findings, detailed in a paper published in Science Advances, highlight a privacy threat that extends beyond conventional camera-related concerns. MIT’s Computer Science and Artificial Intelligence Laboratory (CSAIL) led the research, introducing a computational imaging algorithm capable of reconstructing pixelated images using subtle changes in light intensity detected by the ambient light sensor.
Yang Liu, lead author, and MIT Electrical Engineering & Computer Science Department (EECS) Ph.D. student emphasized the potential misuse of these sensors, stating, “Many believe that these sensors should always be turned on.”
The algorithm demonstrated how hackers could use the ambient light sensor to spy on hand gestures like scrolling, swiping, and hovering. Apps with access to the screen, such as video players and web browsers, could utilize this technique to collect data without user permission, posing a privacy concern.
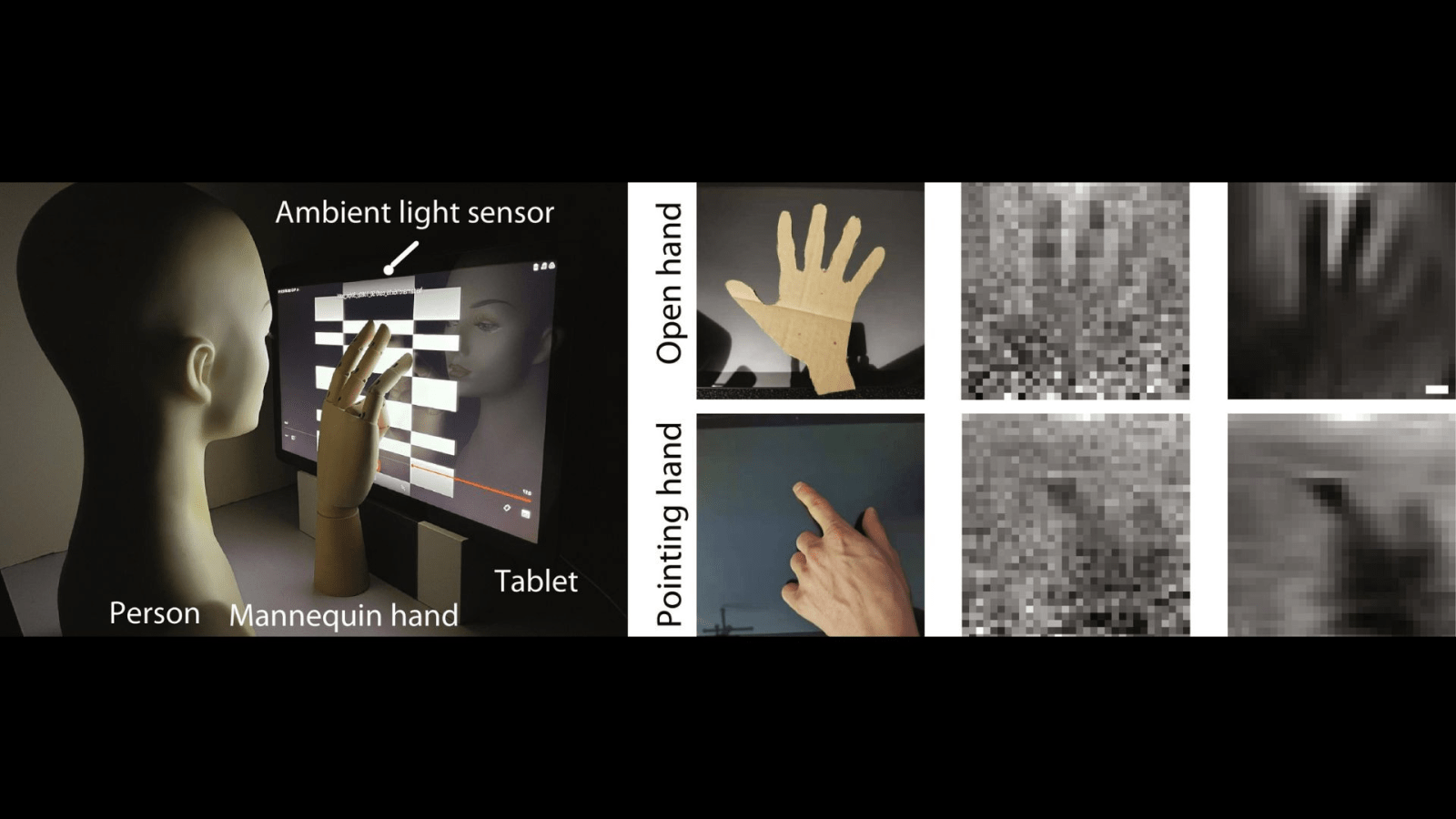
The researchers conducted tests using an Android tablet, revealing the sensor’s ability to capture physical interactions with the screen, track user movements, and even expose touch gestures during video playback. The imaging privacy threat extends beyond the scope of conventional cameras, creating a novel challenge for smartphone security.
To address this vulnerability, the researchers proposed two crucial countermeasures. Firstly, advocating for granular app permissions, users should have explicit control over which apps can access the ambient light sensor. This empowers users to decide who can access their digital lives. Secondly, sensor downgrade involves limiting the sensor’s precision and speed to reduce the amount of information it collects, making it harder for hackers to gather meaningful data.
In addition to software solutions, the researchers suggested a hardware shift by relocating the sensor away from the user’s direct interaction zone, placing it on the side of the device where touch-based information cannot be captured.
Despite the relatively slow image retrieval rate, with one blurry image captured every 3.3 minutes, the potential for real-time eavesdropping with faster sensors raises concerns about digital privacy. This research underscores the need for heightened awareness regarding seemingly innocuous smartphone features and the imperative of adopting robust security measures to safeguard user privacy in the evolving digital landscape.


