According to CNews, which cited a survey released by the Kaspersky ICS CERT global cybersecurity research center, the People’s Republic of China has secretly accessed classified data from servers of Russian industrial sector firms.
According to the report, various Eastern European countries (including Russia and Afghanistan) were attacked in January 2022 by the Chinese-speaking APT organization TA428, renowned for previous similar campaigns against European and Asian enterprises.

The hacking’s main goal was to obtain sensitive secret material, mainly information regarding defense industry projects.
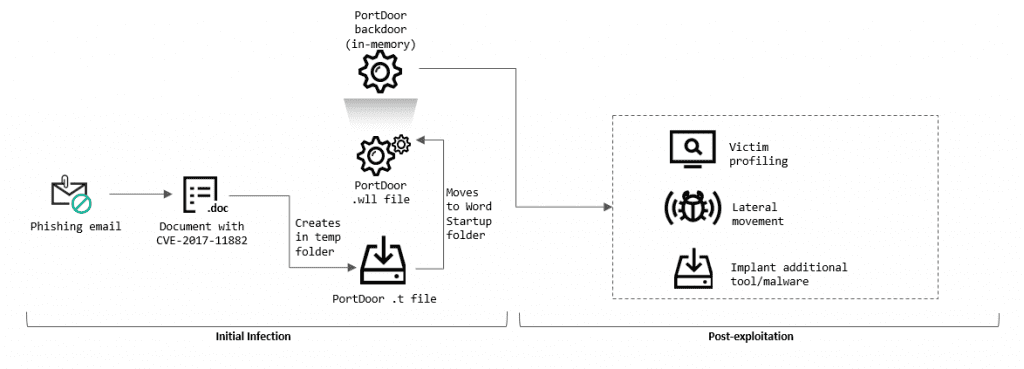
Chinese hackers used phishing emails to install the PortDoor virus, which stole the data. The attack was divided into two “echelons”: the first echelon was made up of many servers from various countries, which sent the stolen files to the second echelon server in China.
Oleksandr Kovalenko, an analyst with the Ukrainian project “Information Resistance,” emphasized that the PRC government funds the TA428 group, making it twice more bitter because Russian state media portrays Russia and China as “sacred brothers and the tandem of the century.”
Also, Chinese TA428 has been spying on Russian ministries, departments, research centers, government organizations, and businesses associated with the military-industrial complex.

“Remarkably, the Chinese hackers carried out their activities for several months, and therefore, one can only imagine how much secret information they got access to,” Kovalenko added.
The entire operation lasted months before it was discovered, making it difficult to establish how much data the Chinese obtained.
Another prominent aspect of the assault is that the phishing emails used in it were “crafted using specific details about the organization’s operation, some of which may not be publicly available,” as observed by the Kaspersky center.

In the analysis, it is stated that “an analysis of document metadata has shown that, with a high degree of likelihood, the attackers stole the document from another military industrial complex enterprise, after which they modified it using a weaponized, a program designed to inject malicious code into documents.
The Kaspersky ICS CERT does not offer a list of the organizations that were the target of this hacking attack. However, according to another expert and the Kaspersky analysis, the attacks were successful.


