Scamming and hacking digital information has been the “thing” of this decade. Whether it is some Nigerian princess wanting to send hundred million dollars to your bank account or it is some technical support staff “kind” enough to be apprehensive about our computers’ slow speed, the examples are too many to quote.
Today, we will identify four of the most common scams prevalent, so that you can be safer and more informed.
1) Microsoft Tech Support
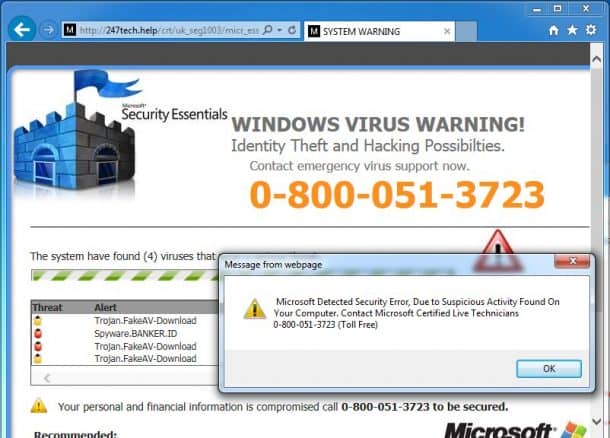
Many of us might have gotten the call from “Microsoft Technical Support Representatives” expressing their concern on how our computer is running slower than usual due to viruses. These people, sitting in some call centre in a third world country use a generic script claiming to resolve the issues if we purchase a piece of software by giving our credit card information over the phone. Sometimes they also try to gain remote access to your PC via TeamViewer. This scam has been so frequent that Microsoft had to issue an official statement on the matter. It read,
“Remember, Microsoft will never proactively reach out to you to provide unsolicited PC or technical support. Any communication we have with you must be initiated by you.”
2) PayPal Dispute Scam
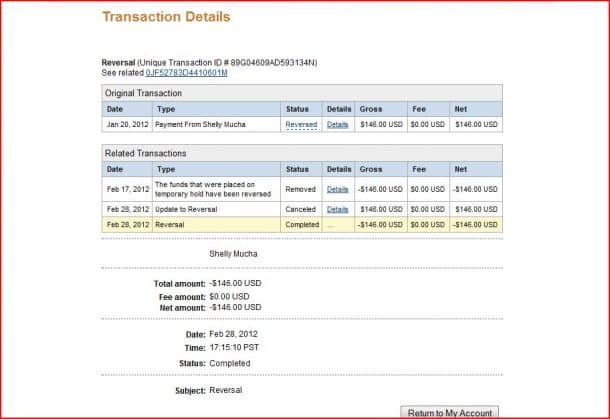
While selling stuff on Kijiji or Craigslist might seem convenient, it is not without its perils and risks. One of the greatest danger involved is the scam involving PayPal payment. Usually, the seller receives a mysterious text message or call saying that they want to pay upfront via PayPal and then pick up the product at a later time. The scam begins once they pick up the product, they tend to open PayPal’s chargeback/dispute option. This gives the “buyer” the leverage to claim that the item was never received and thus they want their money back. And if the seller doesn’t have any legal proof of handing over the item, PayPal always tends to side with a buyer meaning the seller loses out on the item as well as their money. To avoid this, always try to get payment in cash, or at least use a trusted retailer and take legal proof of handing over the item to the buyer.
3) Credit Card Skimmers
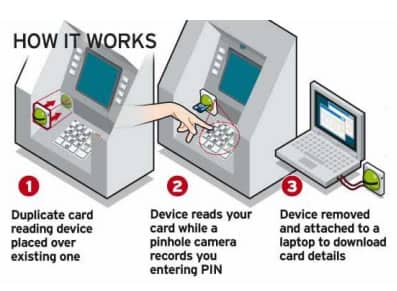
This ATM related scam has beleaguered banks and customers likewise. Usually, the scammers install a skimmer card reader on an ATM that grabs data from a card’s magnetic stripe when you insert your card. A camera is used to records the pin and security code, and after the skimmer is recollected, an attacker uses it to download the data into his computer and create cloned cards. Or he/she can sell the stolen information on the dark web. To avoid this, always make sure that the ATM card reader is secure and looks similar to other machines.
4) Fake Anti-virus software
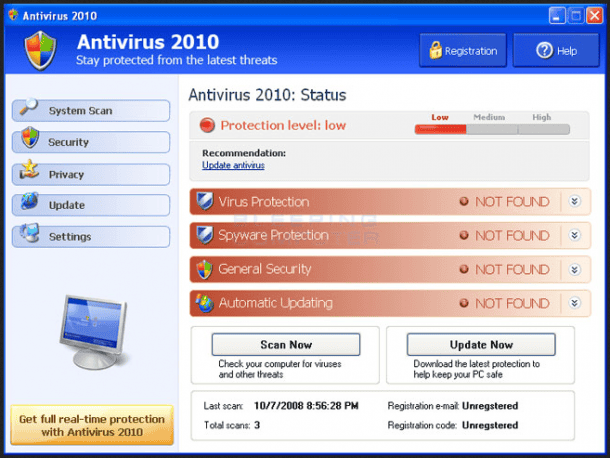
As it turns out, the annoying pop-ups claiming that our computers are infected are not just intrusive and pushy, but are also part of a hacking scam that has been around since the time of Windows XP. It asks you to install its antivirus to remove a random number of viruses, but as soon as you install the software, the computer gets infected by Malware or even a ransomware such as CryptoLocker. CryptoLocker is a Trojan which encrypts all the files on a user’s computer and demands the user to pay an amount of money for the decryption otherwise the files will be deleted within 72 hours. And even if you pay up and gets back your files, the scam can be repeated multiple times as the malware usually doesn’t delete the malware. So, always avoid to download or install any file from an untrusted or unknown source, and if you suspect something fishy, unplug your power or turn off the WiFi to ensure your files are not stolen.
Have you ever been a victim of a scamming/hacking attack? How did you respond to it?
Share your experience in the comments’ section below!


