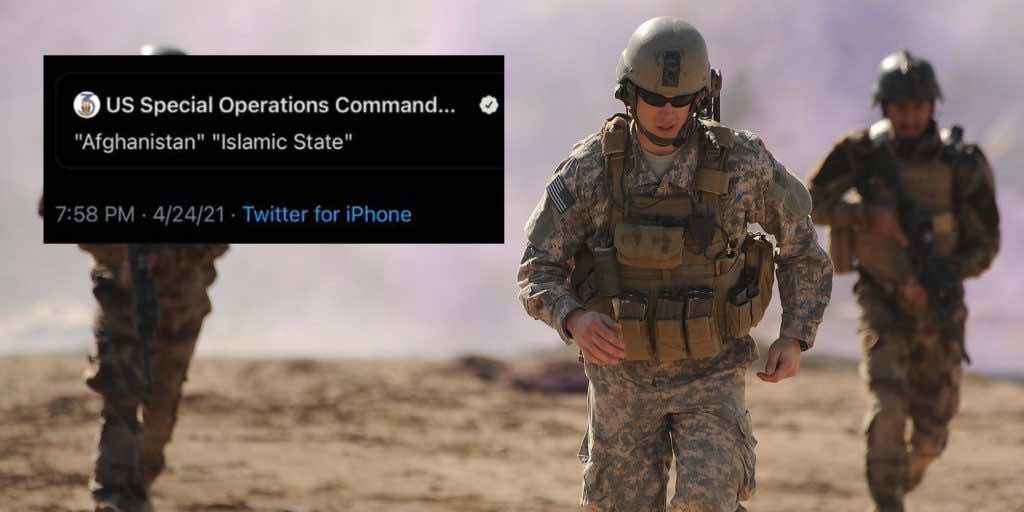
It was US Special Operations Command Centrals turn to be hacked.
A rather sensitive US department published a meaningless Tweet, Special Operations responsible for operating overseas. The tweet stated “Afghanistan” “Islamic State.” As anticlimactic as the tweet was, who knows what kind of chaos can be caused through a single tweet from a sensitive account such as this.
The department later regained control of their account, removed the Tweet, and apologized for the inconvenience caused. However, many journalists and writers have had their fair share of doubts if the account was even hacked. Why waste such an opportunity where you have cracked into a sensitive Twitter account on just saying something bizarre and foolish. And I can not agree on it any less, as if I was a hacker and ever scored an opportunity to cause chaos, why wouldn’t I?
“In the past 12 hours, someone hacked our unit’s official account and tweeted a misleading message. We apologize for any confusion or insensitive content,” tweeted @USSOCCENT.
The department has its headquarters at MacDill Air Force Base in Tampa, and Special Operations Command Central (SOCOM) is its sub-unified command. SOCCOENT plans and conducts special operations overseas, mostly in the Middle East, Central Asia, and South Asia. Formed in 1987, it is the only unified command of all US forces and was formed to carry out better-coordinated missions. The need was felt for such a body after a series of failed missions, including the failed “Operation Eagle Claw,” a disastrous attempt of rescuing hostages from the American embassy in Iran in 1980.
Sabotaging a Twitter account that in some way represents all US military forces is no small deal. Such a hack could lead to massive chaos and unrest, only if it were not used to say “Afghanistan is an Islamic state.” Hack or no hack, the good thing is that there were no threats stated to the human population anywhere because that could be one extreme eventuality caused by such a breach.
Not the first time
This hacking incident, however, was not the first of its kind. Official accounts of sensitive US departments often fall prey to such eventualities. A month ago, a US strategic command official tweeted “;l; gmlxzssaw” and many thought of it as some dangerous launch code, threatening to destroy an enemy nation.
The strategic command is responsible for safeguarding and controlling America’s nuclear weapons, and many were threatened of a mass destruction event to take place. Only to find later that it was a baby that threatened the world of his powers, the incident proved the statement “Youngest is the most mischievous” true.
What actually happened was that the administrator of the Twitter account left his system unattended for a bit, and his youngest child didn’t waste any time and seized the opportunity. He got on the keyboard, wrote in baby language, and pressed the enter key. Pretty unfortunate for the Twitter account manager was that the opened page was also the most sensitive one, not a random google search window. I think of the hard explanations he would have given to his superiors and the scolding the baby would have received after messing up with the daddy’s system.
Later, the post that rang alarms for many was followed by an apology from the USSTRATCOM stating that the account wasn’t hacked; rather, the post was made by mistake and deleted in no time.
However, US Special Operations Command Central kept on the narrative that the Tweet, stating Afghanistan is an Islamic state, was indeed a hacking activity. People who initially assumed the tweet was a blunder said it was more concerning to know that it sure was a hack, leaving the question behind how easy it is to breach a sensitive account, make a false statement on it, and result in havoc.