Amid the spotlight of one of the largest hacking conferences worldwide, an innovative $70 homemade gadget has taken center stage, unveiling a cunning strategy that could potentially lead to surreptitious theft of iCloud passwords and other crucial credentials.
The peculiar-looking device, resembling a creation that the Joker from comic books might employ to trigger a minor explosion, caused quite a commotion at Def Con. It was presented as part of a research project with dual intentions: injecting a bit of humor into the event while also being an important reminder about correctly disabling Bluetooth to ensure iPhone security.
The makeshift device, a brainchild of hacker Jae Bochs, created a spectacle at Def Con by generating pop-up notifications on the smartphones of fellow convention attendees. Comprising a blend of components, including a Raspberry Pi Zero 2 W, two antennas, a Bluetooth adapter, and a battery, the device was ingeniously designed to exploit Apple’s Bluetooth low energy protocols.
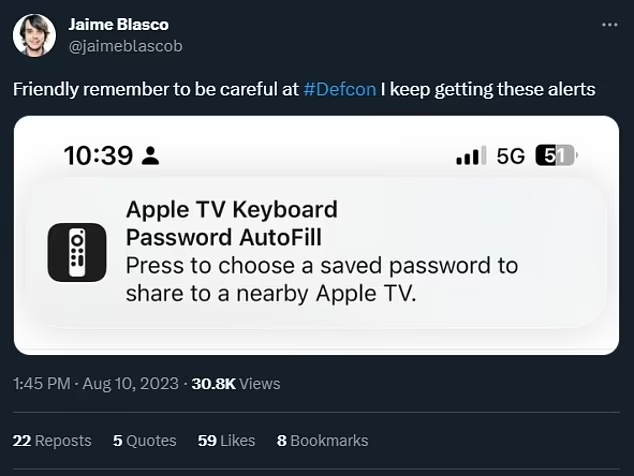
The ingenious concept capitalizes on Apple’s protocol, allowing devices to communicate with iPhones through “proximity actions” that trigger pop-up notifications. In this scenario, the pop-up mimicked Apple’s innovative Apple TV Keyboard Password AutoFill feature, usually enabling users to input passwords for various services like Apple ID and Netflix on their Apple TV using their iPhone’s keyboard instead of the remote’s arrows.
The essence of the concept is that, in theory, a malicious actor could utilize such a device to generate pop-up alerts on unsuspecting individuals’ iPhones. The individuals, momentarily diverted, might inadvertently enter a password without consideration. This scenario underscores the importance of being cautious about Bluetooth settings and exercising caution when confronted with unexpected pop-ups soliciting passwords or login credentials.
The device’s composition, excluding the battery, was estimated by Bochs to cost around $70, possessing a range of approximately 50 feet (15 meters). Bochs’ proof of concept involved crafting a customized advertisement packet that mimics the low-power emissions emitted by devices like Apple TV, inducing nearby devices to display pop-up notifications.

Although Bochs’ demonstration operated as a harmless prank and precautionary exercise, he pointed out that a malicious actor equipped with similar tools could potentially gather data. If a user were to interact with the prompted messages, and the other end responded convincingly, the victim might unknowingly transfer a password.
Bochs expressed skepticism about Apple’s willingness to address this issue. The low-energy protocol’s core programming appears to be intentionally designed to allow devices like watches and headphones to maintain Bluetooth functionality. Despite any inherent vulnerabilities, altering the feature might compromise its intended functionality.
Ultimately, the takeaway from this demonstration is evident: for individuals aiming to fortify their iPhones against potential rogue Bluetooth intrusions like the one highlighted, a thorough and proper deactivation of Bluetooth is essential. Simply toggling the Bluetooth switch in the Control Panel isn’t sufficient, as it still interacts with proximity-activated beacons. To fully disable Bluetooth, users must navigate to iPhone Settings, select Bluetooth, and deactivate the Bluetooth toggle at the top of the page.


