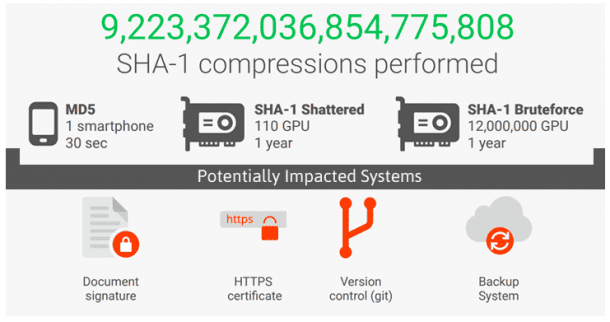
A team from Google and CWI Amsterdam has just announced about the first SHA-1 (Secure Hash Algorithm 1) hash collision. SHA–1 is a cryptographic hash function, which is designed by the United States National Security Agency (NSA) and is a U.S. Federal Information Processing Standard published by the NIST, USA. The attack on the 160-bit (20-byte) hash message digest required over 9,223,372,036,854,775,808 SHA-1 computations, which would take 6,500 years if done on a single CPU and 110 years on single GPU computations.
The sheer numbers may seem too far-fetched, but they are practical if you are, let’s say, a state-sponsored attacker and have a large enough botnet. SHA-1 is used for file integrity verification and digital signatures in a host of applications, such as PGP/GPG signatures, software updates, digital certificates, backup systems, etc.
SHA-1 was brought in as a safer alternative to MD5, which was known to be faulty since 1996. In 2004, MD5 was finally declared unsuited for applications like SSL certificates or digital signatures.
The theoretical attacks against SHA-1 have been on the horizon since 2005, with a practical one demonstrated in 2015. While it didn’t stop the usage of SHA-1 hash function, it still undermined its security claims. But the latest operation, dubbed ‘SHAttered,’ may have drawn the final straw, as it managed to produce two different PDF files with the same checksum.
The working code for the attack will be released in three months complying with Google’s vulnerability disclosure policy, which will allow anyone to create a pair of PDFs that hash and give two distinct images without any specified pre-conditions. Google Chrome is now already warning the users when visiting websites with the SHA-1 certificate and recommends using SHA-256 or SHA-3 on the software.
Meanwhile, Google has released a free detection tool that sorts out whether your files are part of a collision attack. You can download it and learn more about the first collision attack at shattered.io.
What are your thoughts on this incident? Comment below!


