In a disturbing trend reported by security analysts, job seekers are falling prey to a new form of cyberattack dubbed “Dev Popper,” wherein threat actors disguise malicious activities as legitimate job interviews. This technique capitalizes on social engineering tactics, exploiting human vulnerabilities such as trust and fear to deceive unsuspecting victims.
The modus operandi begins with the posting of fake job listings targeting software developers. Once interviews are scheduled with applicants, the attackers orchestrate seemingly innocuous mid-interview tasks, common in the software development field, to assess candidates’ skills.
These tasks involve downloading and executing software from ostensibly reputable sources like GitHub. However, the software contains a hidden Python remote access trojan (RAT) payload that compromises the interviewee’s device upon execution.
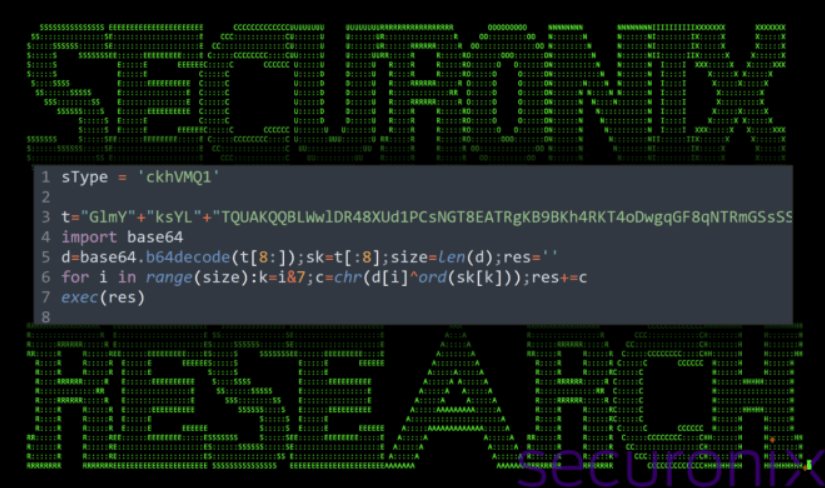
The malicious software, disguised within seemingly harmless GitHub zip archives, utilizes node package manager (NPM) packages. Despite initial appearances of safety, these packages harbor JavaScript files in their Backend directories, employing obfuscated code to download and extract an archive file.
Executing the buried Python code installs the RAT on the victim’s system, initiating data collection and enabling remote control by the attacker. This grants access to sensitive information, including OS type, device UUID, network data, keystrokes, and the ability to execute shell commands.
While the majority of malicious files have been removed from GitHub, similar threats persist within the cybersecurity landscape. Securonix attributes these attacks to threat actors based in North Korea, highlighting the global reach of such nefarious activities.

In light of these threats, Securonix advises job seekers to remain vigilant during interviews, even amidst the pressure to perform well. The guise of professionalism and legitimacy cultivated during the interview process serves to lower victims’ guard, making them susceptible to malware deployment. Refusal to comply with the interviewer’s requests could jeopardize the job opportunity, compounding the difficulty of identifying and thwarting such attacks.
In navigating the ever-changing cybersecurity terrain, vigilance and prudence stand as crucial pillars in defending against nefarious tactics like Dev Popper. By remaining well-informed and embracing proactive strategies, individuals can attenuate the hazards linked with cyber threats, thus shielding themselves from succumbing to such insidious ploys.


