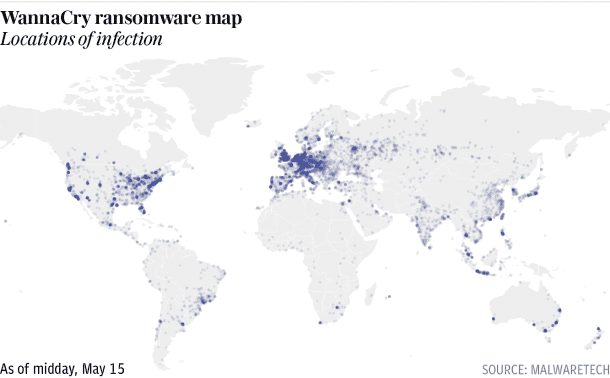
A ransomware attack last Friday brought a disaster for many organizations like FedEx, Telefonica, Russian banks, French car manufacturers, and even the UK National Health Service (NHS) resulting in the cancelation of operations, X-rays, and patient records became unavailable. We heard of such an attack over a year ago but it was not at such a scale. The guy who rose as an accidental hero halting the global spread of the attack was a 22-year-old man Marcus Hutchins.
Hutchins is a British cybersecurity researcher who stopped the ransomware nicknamed “WannaCry” by registering a garbled domain, sitting inside a bedroom in his parents’ seaside resort on the north Devon coast. His bedroom is a small self-assembled IT hub with computer servers, three or more monitors, and lots of video games.
The researcher goes by the MalwareTech on Twitter. While trying to track the virus, he registered a garbled domain name hidden in the malware to his name, halting the attack unintentionally. In a detailed blog post on his website titled “How to Accidentally Stop a Global Cyber Attacks,” he explained all his efforts for making it happen.
He writes on the post, “I was quickly able to get a sample of the malware with the help of Kafeine, a good friend, and fellow researcher. Upon running the sample in my analysis environment, I instantly noticed it queried an unregistered domain, which I promptly registered. We prevented the spread of the ransomware and prevented it ransoming any new computer since the registration of the domain (I initially kept quiet about this while I reverse engineered the code myself to triple check this was the case, but by now Darien’s tweet had gotten a lot of traction)”
The infamous malware “WannaCry” encrypts the data on the victim’s computer and asks for payment in exchange for decryption. Messages from the victimized NHS staff showed the attackers asking for $300 in Bitcoins for the data decryption. According to CNBC, people have paid the attackers nearly $50,000 in ransom so far.
Executive Director Europol Robert Wainwright said that there was a minimum of 200,000 people affected by the malware across 150 countries.